
New SEC rules require business leaders to confront the challenge of providing public investors with visibility into cybersecurity strategy, risks, incidents, and an enterprise’s cybersecurity posture. But cybersecurity posture—an organization’s readiness to successfully defend and protect its digital assets—as it is understood and implemented today is simply insufficient.
With the new SEC rules, in addition to disclosing material information related to cybersecurity incidents, companies must describe their processes for identifying, assessing, and managing cyber threats. Companies also must provide annual details on the role the board of directors is taking to oversee cyber risks as well as management’s role in and capability to manage those risks. Implicit in these rules is the suggestion that the actions of directors and management may be subject to SEC enforcement measures when future cyber incidents occur.
BACKGROUND
Most cybersecurity breaches are not the result of unknown vulnerabilities or novel exploits developed by innovative criminals. Instead, the World Economic Forum found that 95% of cyber incidents result from human failure, (e.g., system users and administrators neglecting to reliably follow well-developed IT/cybersecurity operational practices).
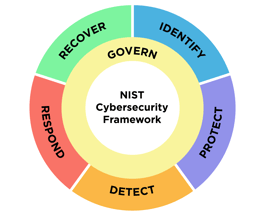 The National Institute of Standards and Technology (NIST) Cybersecurity Framework provides guidance to industries and governments on how to operate and manage enterprise information assets in a manner that minimizes cybersecurity risk. The common enterprise approach has been to adopt standards (like NIST 800.53 or ISO 27000) that contain policies that organizations should implement. This framework is useful, but it is not sufficient to address the risks and threats companies face.
The National Institute of Standards and Technology (NIST) Cybersecurity Framework provides guidance to industries and governments on how to operate and manage enterprise information assets in a manner that minimizes cybersecurity risk. The common enterprise approach has been to adopt standards (like NIST 800.53 or ISO 27000) that contain policies that organizations should implement. This framework is useful, but it is not sufficient to address the risks and threats companies face.
To be effective, the framework requires controls, processes, and procedures. The controls are often provided by technology systems and cloud services, while the processes and procedures use a combination of automation and human-performed tasks. Wrapping around these policies, controls, processes, and procedures are separate governance processes to form a complete system. The system is documented and a NIST or International Organization for Standardization (ISO) compliance auditor periodically audits the documentation.
THE PROBLEM
If the system worked reliably, the number and impact of cybersecurity incidents and breaches would be much lower than we see today. Many cyber breaches happen to companies that consistently pass their compliance audits, which means the framework and system of controls, processes, and procedures are failing to perform as expected.
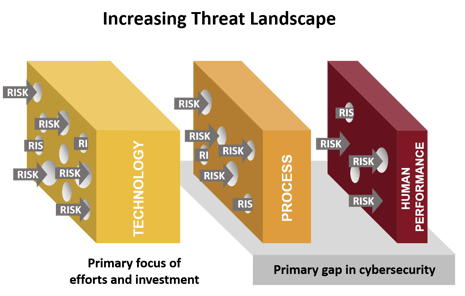 Some argue that the systems are inadequate for the cybersecurity duty they are intended to perform, but 95% of incidents were enabled by someone not knowing what they were supposed to do or knowing and still not doing it right.
Some argue that the systems are inadequate for the cybersecurity duty they are intended to perform, but 95% of incidents were enabled by someone not knowing what they were supposed to do or knowing and still not doing it right.
Compounding this problem is the fact that organizations are operating with the incorrect assumption that their cybersecurity systems are doing the job they expect. The average time between breach and detection in 2022 was 277 days, and when the breach involved stolen or compromised credentials, it took an astonishing 327 days to detect!
The current approach to cybersecurity fails to address today’s (and tomorrow’s) cyber threats for several reasons:
- Complexity is rapidly increasing in IT environments that must be protected (complexity erodes the ability of discrete policies, processes, and procedures to mitigate the threats—it’s simply not possible to imagine and predict all of the ways the systems can fail)
- A pervasive lack of formality in how IT operators and users work undermines effective governance
- Understaffing, significant skills gaps, and overworked technicians undermine process discipline and erode cybersecurity system effectiveness
- Processes and procedures underpinning cybersecurity systems are not designed to be resilient in the face of human fallibility
- The culture and operational environment in IT organizations do not leverage the principles of high reliability
Without significant improvements in these areas, enterprise cybersecurity will continue to fail. Worse yet, it may deteriorate further with the introduction of Zero Trust Network Architecture (ZTNA). Despite ZTNA’s indisputable potential to reduce cyber risk, without the right processes, procedures, and governance—and the ability to reliably execute them with real operational discipline—the additional complexity that ZTNA brings will likely introduce a host of unrecognized and unmanaged risks to IT operations.
THE SOLUTION
The practices and principles of High Reliability Organizations (HROs) have, for decades, been successfully used to mitigate risk and add resiliency in complex, high-risk environments (such as nuclear power, commercial and military aviation, oil and gas exploration, extraction, refining, and transportation, chemical manufacturing, and healthcare). But they have never been applied to reducing risk in the digital domain—until now.
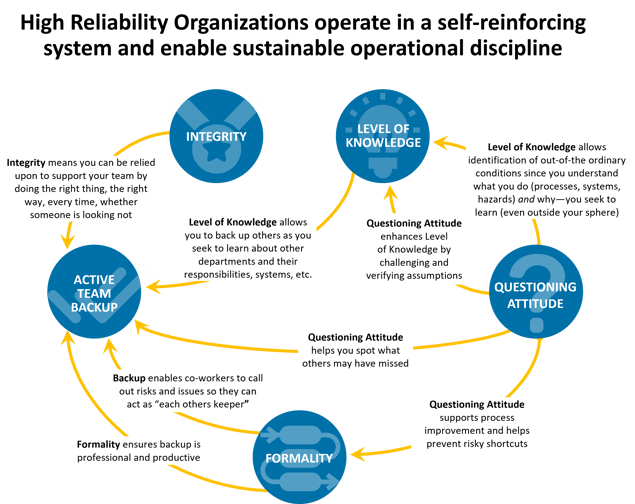
Wilson Perumal’s High Reliability Cybersecurity (HRC) and High Reliability ZTNA (HR-ZTNA) offerings are designed to address this gap by applying the proven approaches of HROs to digital operations. Our approach enables a high reliability cybersecurity posture that can:
- Manage the growing impacts of complexity on IT and cybersecurity operations
- Improve cybersecurity system resilience
- Improve human performance and operational discipline in the digital domain
- Improve governance effectiveness
By employing HRC and HR-ZTNA, leaders of publicly traded enterprises, private companies, and government organizations can confidently demonstrate they have a robust cybersecurity system that incorporates the proven principles of high reliability. High Reliability Cybersecurity Organizations (HRCOs) don’t just rely on policies, procedures, and technology solutions outlined in standards by organizations like NIST and ISO. Instead, HRCOs take proactive steps to ensure those policies and procedures are resilient in the face of human failure, and they leverage a proven culture of operational discipline.
HRCOs are experts at detecting and acting on issues before they become incidents and breaches. They are organizations that learn quickly and maintain a high level of functional expertise at all levels. Leaders in HRCOs operate with confidence knowing they have an entire team capable of executing their cybersecurity system and aren’t reliant on just a few key, often overworked, individuals.
With the principles of high reliability underpinning their cybersecurity system, HRCOs are best positioned to defend against current and future cyber threats. The new SEC regulations place new requirements on companies and leaders to address the areas where failures continue to happen. Directors and officers of HRCOs can rest well at night, assured they are doing all they can to protect their company and themselves against regulatory (and potentially criminal) liability.
