Protect Your Company from Cyberthreats Targeting Remote-Work Vulnerabilities
- Remote work enables cybercriminals to exploit system weaknesses and insufficient security systems/protocols
- Human performance is the most critical line of defense—breakdowns in human performance cause 95% of cybersecurity breaches
- It is critical to assess your organizational resilience to cyberthreats and address weaknesses now—which will pay off during and after the crisis
Cybercriminals are increasingly exploiting vulnerabilities created by the rise of remote and hybrid work. Less oversight and fewer security defenses, plus the heightened level of collective anxiety, means people are more likely to fall prey to social engineering scams.
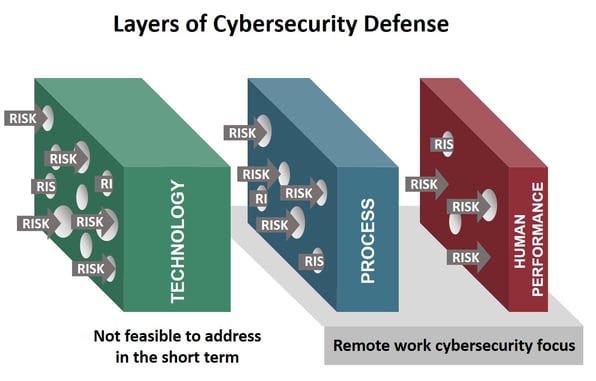
It is critical to take two sets of actions. First, upgrade your security protocols for the new work-from-home dynamics. Second, assess your organizational readiness to defend against cyberthreats along three lines of defense: systems/software, processes, and (often most important and overlooked) human performance. Measuring your company’s alignment with the behaviors of High Reliability Cybersecurity Operations (HRCO) allows you to identify vulnerabilities due to human performance and develop new lines of defense.
Take these “no-regrets” actions to upgrade your security protocols:
- Put key remote-working security protocols in place—provide employees with clear instructions and explanations
- Keep endpoint security and VPN technologies up to date and ensure use
- Increase Internet bandwidth and perimeter security capacity (firewall, IDS/IPS, etc.)
- Employ multi-factor authentication and renew expiring credentials to strengthen identity and access management (IAM) capabilities
- Ensure cybersecurity processes/policies are monitored and enforced
Assess your organizational readiness to defend against cyberthreats and identify gaps—then implement mitigation and human performance improvement actions. WP&C’s online tool, Yardstyck, helps leaders:
- Assess employee behaviors and attitudes against those of HRCOs
- Identify gaps in cybersecurity-related human performance by employee group, geography, business unit, etc.
- Develop and implement risk mitigations to address human performance gaps such as training, information sessions, and online workshops
Adopting HRCO principles now will provide a critical boost to cybersecurity at this time of unprecedented vulnerability and lay a strong foundation for post-crisis cybersecurity.